Step #1 - Secure Your Email. It's easy.
We use real servers based in Zurich, Switzerland. There is not a better email solution today. And, it's open-source. That's a really big deal when it comes to security.
We are actively setting up family and business domains that include email, calendar, contact and to-do and is an Exchange-like experience, but without the bugs and transparency of the public email services like #gmail and #yahoomail .
Step #2 - Secure Your Online Presence.
First, a couple of definitions.
Privacy - when they know who you are, but not what you are doing.
Anonymity - when they see what you are doing but not who you are.
Ideally, you want both, every step of the way. Tor, for example, provides anonymity and a VPN, for example, provides privacy. But there are many more links in the chain and each must be as robust as the last.
Securing your online activity also includes anti-virus and malware, intrusion prevention, a firewall, anti-spam engine, and browsing protection. And, very importantly, immediate updating of operating system and 3rd party software applications. The fact is, most intrusions could have been prevented with current software patches and updates. With Microsoft, this is practically a full-time job but with our system, it's monitored and automated, never skipping a beat.
Here's how;
Large institutions have long recognized the value and potential liability of their digital assets and have invested vast sums of money to protect themselves from the associated risks. It's still a whack-a-mole game at that level and always will be, and this is precisely the point; this tension between the institution and the hackers is an amazing and energizing force that has created remarkable innovation and solutions that become evermore robust and inexpensive. It is a fact of physics that technology gets better at an exponential rate and cheaper just as quickly. If you don't know Moore's Law, honestly, it's time you do because not only is the rate of change getting faster but so is the rate of the rate of change. When it comes to math, that's a huge phenomenon.
http://en.wikipedia.org/wiki/Moore%27s_law
Check this graph out;
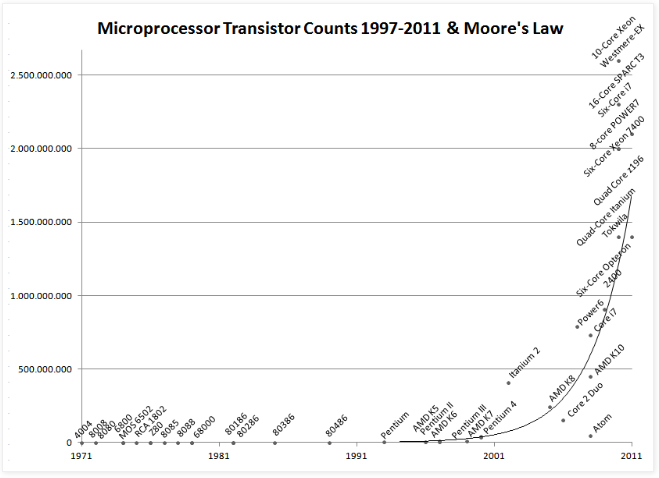
The graph illustrates computer performance from 1975 to 2011. The crucial point here though is that we are now in the zone of the "hockey stick". That's where the line starts to go vertical. Since the computer chip was invented it has been evolving at a rate previously unheard of in any activity. The accumulation of these exponential gains (think compound interest rates) put us at a point, right now today, where the rates of change are literally going vertical, like straight up. That's the hockey stick piece. If you take one thing away, take this; you ain't seen nothin' yet. This is not "bad" news, it just is what it is but it could be tragic if you don't recognize it. And, what Step #2 is all about is using this awesome progress in technology by leveraging it's performance and ridiculously low prices to your advantage in the realm of your personal security and privacy.
OK, so, back to securing your online presence; it is all about taking the solutions provided at the institutional level and engineering them for the individual consumer. That's you and me and our families and our offices. This is precisely what we do for our customers. At this level of protection security is operated as a service, as opposed to a product. "Products" are installed and expected to go to work. Today's cyber-environment requires a more dynamic process of monitoring, assessing and adapting. For this we use a network ops center in Helsinki, Finland, (another country that is maniacal about privacy rights) operated by the F-Secure company. They are the real deal, check them out. The monitoring is 24/7/365 and defenses are automated, including software patches and updates, anti-virus and malware, intrusion prevention, a firewall, anti-spam engine, vulnerability testing and browsing protection.
Step #3 - Secure Your Digital Assets.
Have you noticed the price of a bitcoin? In less than a year it's gone from $10 to $1,000, in round numbers. I don't know if this tulip-mania and I don't really care because it's a symptom. The cause of this phenomenon is the rapidly increasing value to anonymity. It's supply and demand all over again. Anonymity is so valued now because their is so little of it left. The inherent value to anonymity is the information behind the curtain. Everyone wants it. Your government is just taking it, the corporation is suckering you into giving it to them and the criminal is stealing it from you. All at the same time. The scarcity of today and the foreseeable future is privacy and anonymity. This makes me laugh because it used to be so valuable to be famous! Perhaps one day we will all have our 15 minutes of pure anonymity. Like a surreal bliss I suppose.
So the point is to secure your stuff. All your digital stuff, because it's becoming more valuable to someone somewhere more and more every day. And this can be tricky.
This is why so much is "free" on the internet. Free social media, email, storage, and the rest. You name it and the billionaires of silicon valley want you to give it to you. Because they are nice guys you suppose? Maybe they are, some seem like it, but we know they aren't "giving" you something without coming out the winner in the exchange. That's what billionaires do really, really well. Remember; if you aren't paying for the product, you are the product. The billionaires made in silicon valley over the last several years have done it faster than ever because they have figured out how to get you to work for them, everyday, and to have you pay them for doing it. No wonder they got so rich so fast. Imagine having millions of others doing your work for you, giving you their stuff, and then paying you for the privilege. That's the dominant business model for the time.
Do what I did and what I do for others; create a digital "Family Vault". Base it in on real servers, offshore, Switzerland or Finland preferably, and encrypt the hell out of it. Create access and user permissions and you then have a family that collaborates around their digital assets. Decades of photos, scans, movies, financial records, legal documents, passwords, ... you get it. Sync and backup is a cinch, legacies are assured and future generations will always have their "digital fort" because we do it in open-source. Like our email solution, our storage solution is open-source and this means you are always portable and format compatible.
You know, at first draft I was going to say 3 "Simple" or "Easy" Steps to Online ... as the title but I couldn't get honest with the words "Simple" and "Easy". We simply, aren't there, yet. That's why we are here, do it for you. And I see our entire service operation as open-source too. We only apply the best-in-breed technology to our solutions and when the title of "best" changes hands, well we do too. We have put together an amazingly robust, effective and affordable system that will not just survive the challenges of change but will thrive on them as well. With our service, the awesomeness that is the nature of technology will be leveraged for the sake of protecting you and those around you, 24/7/365. This is effective risk management for the digital age.
Thanks for reading,
Brad



